Hi guys, Long time no see, ‘was been busy with placements , FYP, people bragging about the offers they’ve got, really Sick time.
Recently i’ve been questioned by the University at the project review for choosing a project in a computer science stream besides i’m being in EEE. To prove them that it was not merely a computer science project i did some research ,and guess what it was astonishing; I’ll share few details about it in this article.
With the Advancement in Technology and Internet flourishing people want all their products ranging from IPOD to SUV’s, Microwave oven to toilet closet :P, Connected to the Internet, so that they could access/control/monitor it from anywhere. The advancement in technology had not only changed the public’s mindset but also the corporate’s mind set too. Now days every manufacturing process in a Industry are controlled by automated systems [Industrial Control Systems (ICS)/Supervisory Control and Data Acquision Systems (SCADA)]. These ICS are also SOMETIMES connected to the Internet. I still could not figure out why the hell they do it. A typical Industrial Control System Network will be like this [It might be a bit complex, but this is a

Skeptical representation of it.] The RTU’s [Remote Terminal Units] are now usually PLC’s [Programmable Logic Controllers, which is an hybrid RTU with reprogramming capablities] , To be simple PLC is something like an advanced Microcontroller which could directly interact with the Industrial Components like Boilers, Pressure Sensors, Turbines etc. DAS is usually a database server which is used for data acquision.A typical Data logged into DAS will be something like, boiler temperature,pressure with respect to time and some other necessary parameters.
HMI [Human Machine Interface]: It is a central Server with huge monitors connected to it displaying various process on going in the plant.It is also used to command and control the PLC’s.This HMI’s nowdays comes up with a webserver like setup, so that the supervisory team of the Powerplant/Industry could connect from their desktop to this HMI server. Sorry for boring u guys, i know, an electrical engineering lecture will always be vague, lets get into the security part.
My aim was to prove that SCADA systems would pose a huge risk if the network admin was obsolete to block internet access to HMI’s or even to some other controllers.
Day1: Started Searching For SCADA systems, it was something like searching a nano particle in a ocean.Tried of using Google. Later that day i came to remember something which i really missed for a long time, and its none other than the SHODAN search engine. I was glad to see that someone had already posted the search queries for several SCADA systems in Shodan’s popular search tab. I took Schneider’s tac xenta controllers as a test sample for my research. And Day1 ended with a bunch of IP addresses from SHODAN.
Tac xenta is a product of Schneider electric which acts as a controller/connecter for numerous RTU’s running over MODBUS/C-BUS/BacNet and a variety of protocols. It collects the data from these devices and integrates it with LonWorks to provide a real time feed of what’s happening in the infrastructure.
Day2:Tried logging into it with some common passwords, scanned with nmap, everything ended up in vain. Suddenly i thought of an idea, why not try finding the documentation of the product, as the exact version number is being displayed on its login page. Before Proceeding further i was day dreaming of myself social engineering the company’s marketing team to handover their documentation of the specific version of their product by impersonating myself as a potential buyer. But sadly i was able to find out the product’s documentation by just googling it [Tac xenta 913]. I was able to see the default password after reading some quarter of the documentation.On testing the default password with the bunch of targets i had, many systems granted access to it.After reading the documentation i learned that, that device also comes with a ftp server.
ftp> open X52.X.1X.2X Connected to X52.X.1X.2X. 220 FTP Server Ready User (X52.X.1X.2X:(none)): xxxx 331 Password required Password: 230 Logged in ftp> dir 200 OK 150 Opening connection drwxrwxrwx 1 usr usr 0 Jan 01 00:00 ram drwxrwxrwx 1 usr usr 0 Jan 01 00:00 sys drwxrwxrwx 1 usr usr 0 Jan 01 00:00 www drwxrwxrwx 1 usr usr 0 Jan 01 00:00 mmc drwxrwxrwx 1 usr usr 0 Jan 01 00:00 configdb drwxrwxrwx 1 usr usr 0 Jan 01 00:00 wm drwxrwxrwx 1 usr usr 0 Jan 01 00:00 tmp drwxrwxrwx 1 usr usr 0 Jan 01 00:00 user drwxrwxrwx 1 usr usr 0 Aug 21 12:41 inet drwxrwxrwx 1 usr usr 0 Apr 23 09:11 fb drwxrwxrwx 1 usr usr 0 Jan 01 00:00 event 226 Closing connection ftp: 458 bytes received in 0.02Seconds 26.94Kbytes/sec. ftp>
This is the web management console of the Controller.
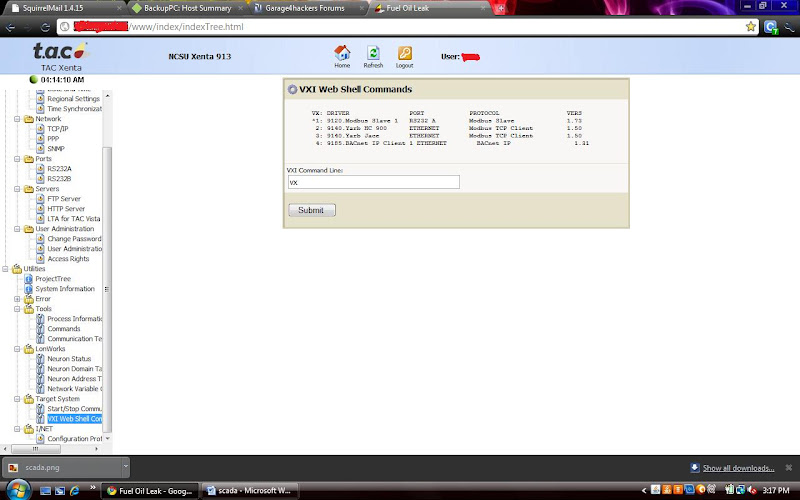
So if it is this simple to intrude and take over a Industrial Control System or a Home Automation system or at least a part of it, Stuxnet is too small to worry. Seems Die Hard 4.0 will no longer be just a science fiction movie, reality is on the way.